|
 |
1919 CE
Arvid Gerhard Damm applies for a patent in Sweden for a mechanical rotor cipher machine. |
|
|
|
|
 |
 |
1919 CE
Gilbert S Vernam patents a teletype encryption machine in which a previously-prepared key, on paper tape, is combined with a plaintext message to produce the ciphertext. To decipher the ciphertext, the same key is applied to the ciphertext, producing the plaintext. |
|
|
|
|
 |
 |
1919 CE
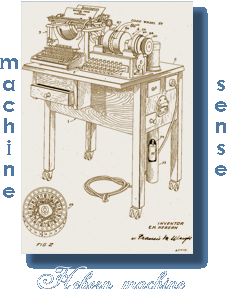
Edward Hugh Hebern patents the Hebern Rotor Machine, the first rotor machine for encryption. |
|
|
|
|
|
 |
1919 CE
Hugo Alexander Koch files a patent in the Netherlands for a rotor based cipher machine. |
|
|
|
|
|
 |
1923 CE
Arthur Scherbius incorporates Chiffriermaschinen Aktiengesellschaft to make and sell Enigma machines. |
|
|
|
|
|
 |
1924 CE
Alexander von Kryha produces a cryptographically weak encryption machine that is used even into the 1950s. |
|
|
|
|
|
 |
1927 CE to 1933 CE
Illigal rum-running is prevalent during the US Prohibition Era. Rum runners use coded messages extensively. As their operations grow more profitable, the codes and ciphers used become more complex. |
|
|
|
|
|
 |
1927 CE
Hugo Alexander Koch |
|
|
|
|
|
 |
1929 CE
Lester S. Hill publishes Cryptography in an Algebraic Alphabet in which a block of plaintext is enciphered by a matrix operation. |
|
|
|
|
|
 |
1930 CE
The American Sigaba Machine (M-134C) is invented. |
|
|
|
|
 |
 |
1930 CE
The Typex encryption machine is invented. |
|
|
|
|
|
 |
1933 CE
Enigma broken by Polish mathematician Marian Rejewski. |
|
|
|
|
|
 |
|















