| P e n T e s t » F o o t p r i n t i n g |
||||||||||||||||
We're an information economy. They teach you that at school. What they don't tell you is that it's impossible to move, to live, to operate at any level without leaving traces, bits, seemingly meaningless fragments of personal information. Fragments that can be retrieved, amplified. |
||||||||||||||||
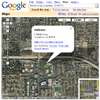
| Footprinting is a preparatory phase of an audit or an attack. It is a type of reconnaissance that involves only non-intrusive information gathering. The target organization is neither actively attacked nor actively probed. How much information we gather at this phase depends purely on the information dissemination habits and publicly available data of the target organization. Together with scanning and enumeration, we obtain a blueprint of the target organization. We use the information collected to narrow the scope of our attack or audit. Target's Internet Presence The target organization may have a website listing company profile, contact information (employee names, addresses, phone numbers and email addresses) and publicity material. Failing that, corporate information can be obtained from public sources, such as Edgar Online. Feeding any of that information into search engines yields even more information, especially if you know how to search, where to search and what to do with the search results. Google hacking is really just a fancy way of saying "using Google while under the influence of your brain". No, really. If you know how to use search operators, and know what phrases to look for, you can actually obtain password files, logs, backup files, server vulnerabilities, online devices... all because the Googlebot managed to catalog data carelessly left somewhere on a web server. Using an offline browser, you can download an entire website onto your local hard drive and peruse it at your leisure. The offline browser will spider down as many levels as you specify and download every file and directory that it can find. Now, even if the target organization has been careful not to allow search engine robots to catalogue sensitive stuff, useful footprinting data still has a way of leaking out into the open. I recall a case where one of my corporate clients had bought and deployed an enterprise-level identity management solution in their office network. They were quite pleased with the system and used it for a number of years. The vendor proudly listed my corporate client as a customer on their website and advertising materials. Here's why this was a problem: A Google search for my client's company name returned the identity management vendor's website among the top 10 search results. A potential intruder, diligently doing his or her homework, could have easily discovered this bit of info. Having identified the identity management software that was in use at my client's network, this intruder could now adapt their attack to target the known vulnerabilities. It may look like harmless, unavoidable data dissemination, but it provides a springboard for further attacks. Here's another example: I can browse the corporate website and retrieve their publicly available street address. I then feed that address into Google Maps and get a satellite image of their premises and the surrounding area. This might give me the placement of dumpsters and security fencing, which will be useful preliminary information for a physical attack such as dumpster diving. Even if the target is a person, they too may have an Internet presence. Searching for their full name may yield phone numbers, personal homepages, blogs, photographs, addresses, online handles, even old USENET posts. This gives you background info and the contact information can also be used to launch further attacks such as social engineering. Google Groups provides an archive of USENET posts dating back to 1981. Back then, Usenet had a much smaller user base, and many of us posted with our real names and email addresses. Some of us still do that today, but with a heightened awareness of the increased number of eyeballs in the readership. Have a look at Linus Torvalds posting in comp.os.minix in 1991. People have a tendency to use the same email address (or the same username) for multiple purposes. Performing a search on an email address or an unusual username can sometimes yield unexpected information. I recall an incident, well-chronicled in the crimeblogging arena, where a professional child caregiver utilized an unusual username in his personal blog. A person using the same username posted messages at a NAMBLA-esque forum. The personal details posted in both the blog and the NAMBLA forum showed startling parallels. But was it all just a terrible coincidence? Hacktivists did a little more digging and managed to verify that the two personas were indeed the same man. They then contacted the man's wife, whereupon the manure hit the ventilator. IP Address Blocks From the IANA: IP addresses are assigned in a delegated manner. End users are assigned IP addresses by their Internet service providers (ISPs). ISPs obtain allocations of IP addresses from a local Internet registry (LIR) or national Internet registry (NIR), or from their appropriate Regional Internet Registry (RIR):Generally speaking, if you have the target's unspoofed public IP addresses, you can figure out their geographic location, ISP and probable default gateway. If you understand IP addressing, spoofing and routing, you can fully utilize ping and traceroute in your information gathering activities. Domain Name System (DNS) Running a whois query against a domain name will yield information about the registrant, administrative contact, technical contact and name servers. You can even see when the domain registration expires. This information can be used as a springboard for further, more focused attacks such as social engineering. Some registrars now offer Private Whois services, where the whois information listed is that of the registrar and not the actual registrant. More information can be gleaned from the DNS zone records. Whether you are simply querying the DNS server for zone records, intercepting DNS zone replication, or even setting up an unauthorized DNS zone transfer, once you have obtained DNS zone information, you are on your way to mapping the target's DNS namespace. DNS was not built for security. It is vulnerable to packet interception, ID guessing, query prediction, name chaining, compromise of trusted server, DoS attacks and authenticated denial of domain names. DNS Security Extensions (DNSSEC) solves some of these issues, but your first priority should be to harden your DNS servers. For starters, don't allow zone transfers to unauthorized DNS servers. Try to segregate the namespace into private and publicly-available zone information. Nslookup, a command-line utility that is available by default on many OSes, allows you to make whois queries. The syntax is fairly easy to understand, but if you do not understand DNS at all, I have listed a few easy-to-use GUI-based whois tools in the next section. Useful Tools Want to identify the sender of a spoofed email? Want more info about the source addresses of traffic on your network? Then you might find it useful to be able to identify the geographic location of an IP address range, or do a little name resolution and maybe snaffle the DNS forward lookup zones of a particular organization. These tools are especially useful for elaborating on the names and numbers:
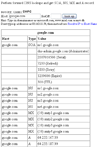
Screenshots of various tools in action:
Further Reading My networking students will no doubt remember vividly the lessons on IP addressing (all those terribly exciting binary-to-decimal conversion exercises) and DNS (particularly the lesson with the Nerf football). Armed with such knowledge, your utilization of the tools listed above is greatly enhanced. In addition, I recommend that you familiarize yourself with the following:
|